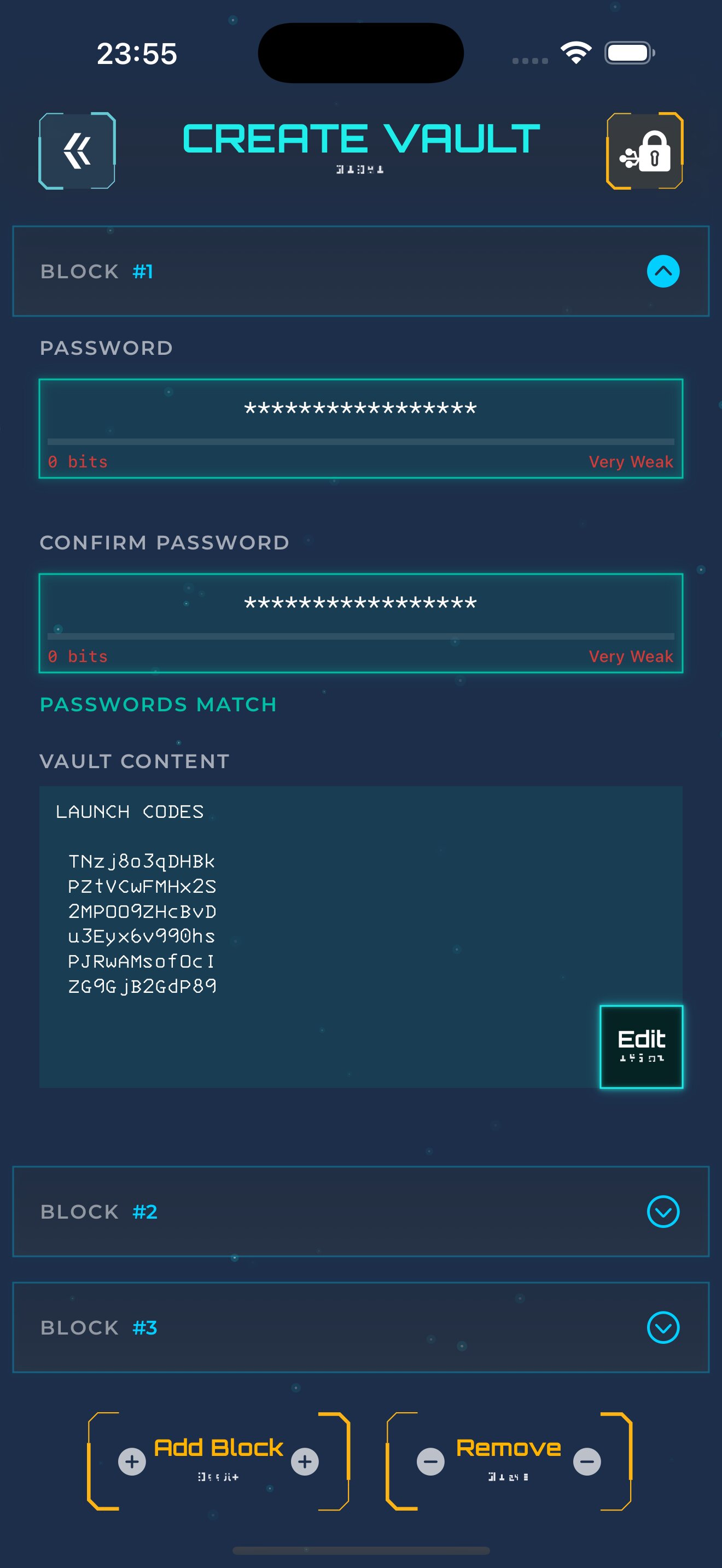
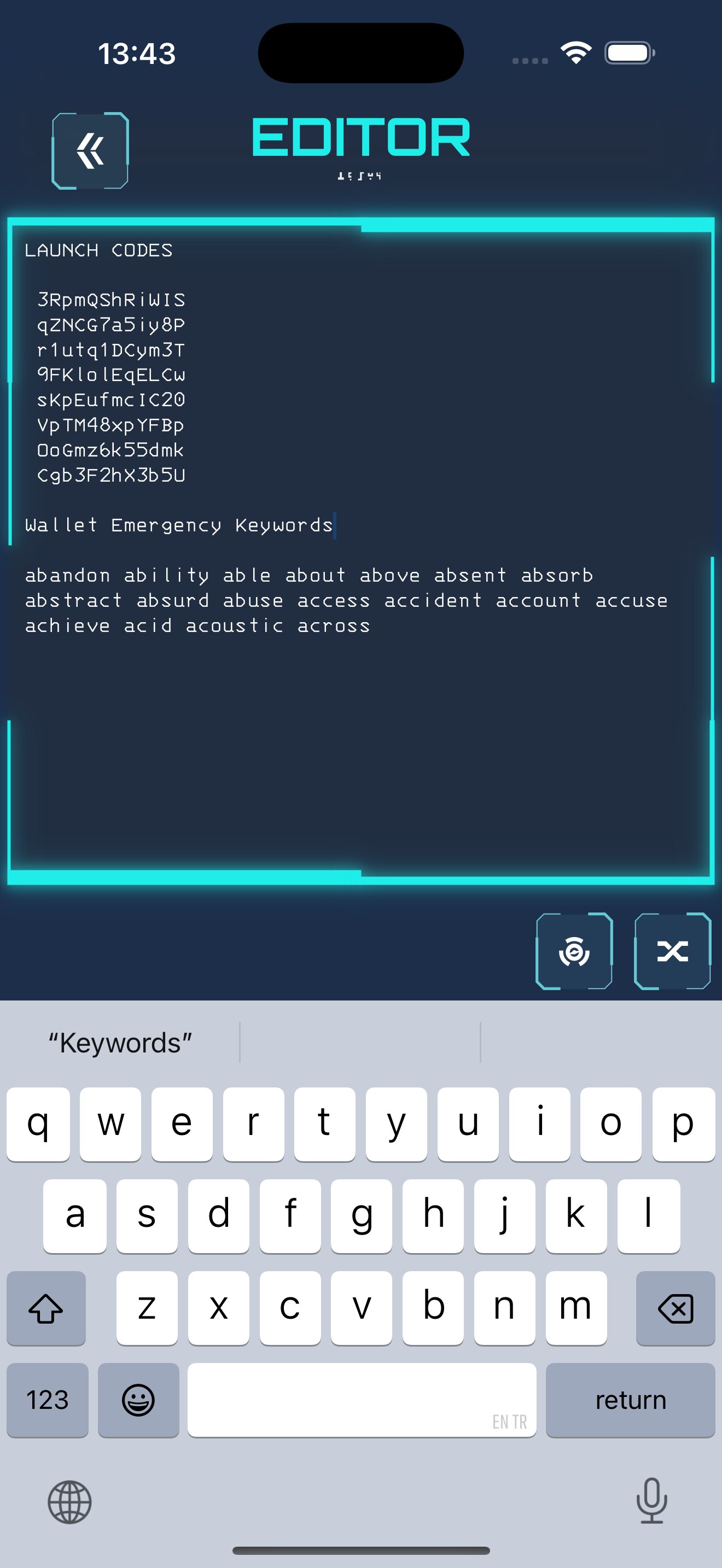
Forced to Unlock?
Veilith Shields Your Secrets
Under coercion, Veilith lets you show them fake data instead of your real secrets. Your actual private information stays completely hidden and undetectable.